Technical explanation of Two-Way-Authentication; Linking DID with Website Origin
By Vishwas Anand on 2022-06-22
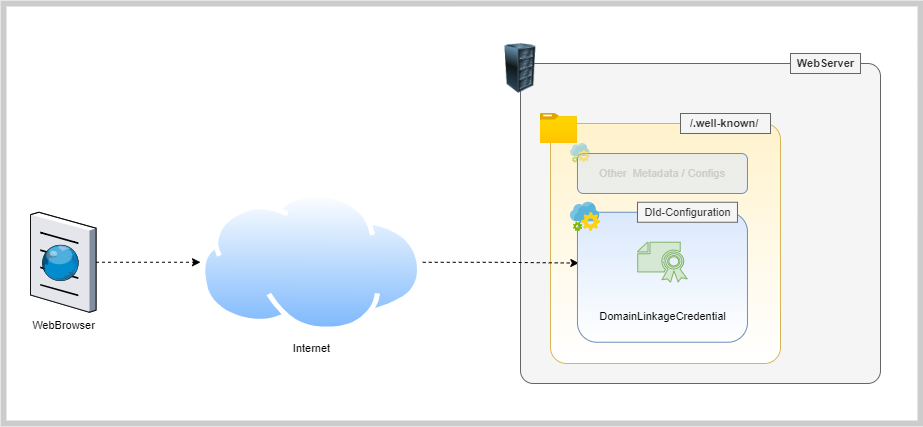
Two features we proudly announce on our website are; Two-Way Authentication and Independent Verification. We will talk about the latter in some other blog but for this blog, let us just stick to the feature - Two-Way Authentication. The question is what is this feature and how it can be technically implemented and proven that it MAY help to stop phishing attacks. Two-Way Authentication Traditionally, when a user tries to log in to a website through a thrid party auth provider (or Identity Provider) like Google Login or Facebook Login, a user is asked to allow access to his/her data by showing him a popup.
Pay per API Call Protocol - Part 1
By Vishwas Anand on 2022-05-18
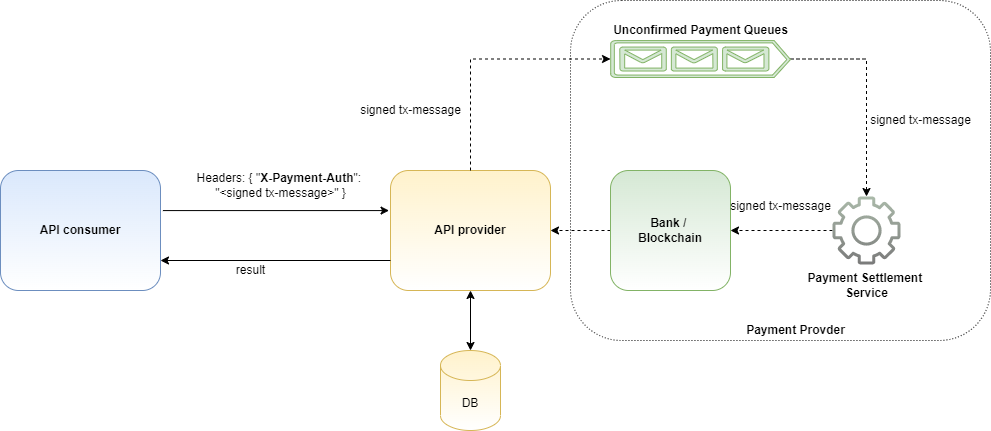
NOTE: This is just my imagination without doing any proper research either on the problem statement or on the protocol. I request you to read this blog keeping that in mind. This is NOT full proof solutinon. Applications share data with each others via APIs. Sometimes, these APIs need to protected behind paywall by the API providers. This is to ensure APIs consumers do not misuse APIs as well as to incure cost of the API services.
Cosmos Modules, Part I : staking, distribution and slashing
By Arnab Ghose on 2022-04-13

Staking The x/staking module handles operations related to staking. Let’s undestand Staking modules with an account being made as a validator and then perform operations related to modules. Creating a validator hid-noded tx staking create-validator --amount=5000000uhid --from=node1 --pubkey=$(hid-noded tendermint show-validator --home=$HOME/.hid-node) --moniker="node1" --chain-id="hidnode" --commission-rate="0.1" --commission-max-rate="0.2" --commission-max-change-rate="0.05" --min-self-delegation="5000" --keyring-backend=test --home=$HOME/.hid-node --yes Here, we have user with account name node1. The user becomes the validator by staking 5000000uhid in the chain. We can the node1 being created as a validator
Paying transaction fee on behalf of someone else!
By Arnab Ghose on 2022-04-13

Building a UX where a User feels comfortable in interacting with the blockchain is much needed. In this blog, we will be looking at how the authz and feegrant Cosmos SDK modules aim to build a similar User Experience. The authz module grants and revokes permissions to accounts for performation certain transactions. This could be token trasnfer, staking. The generic authorization is where we can explicitly pass the TypeURL of the transaction, which is going to be our focus for this blog.
Inflation in the Cosmos Ecosystem
By Arnab Ghose on 2022-04-11

We are quite familiar with what inflation is in real life. When the supply falls short of demand, the cost of goods and services increase, thus inflation. You can read more about inflation here. But what does it really mean in the world of Cosmos? Unlike real world, Inflation in Cosmos refers to the increase in minted tokens for each block, which are used to incentivize the stakeholders. Cosmos SDK allows us to set the parameters for initial inflation rate and the paramters related to it.
Avatars May Use SSI In Metaverse To Prove Identity
By Vishwas Anand on 2022-01-07

Image Credit: https://www.verizon.com Introduction Metaverse has been in the news for quite some time now. Seems like the next “buzzword” after “blockchain” in the tech space. The tech got a surge especially after Facebook decided to change its name to Meta. In this blog, we will understand what is Metaverse (a very basic intro) and its relationship with digital identities. The focus will be on explaining why decentralized digital identities are an important tool for Metaverse to replicate the real world.
Introduction to Inter-Blockchain Communication (IBC) Protocol
By Arnab Ghose on 2022-01-04
At Hypersign, we are working towards building our network and researching about some of the popular frameworks to choose from. Cosmos and Polygon are top on our list. A quick bite about the Hypersign Network before we move on: Hypersign Identity Network - A simple, secure and affordable blockchain network for managing digital identity and access rights without compromising on security and privacy. The network also incorporates privacy subchains and interoperability between them.
Automation Testing with No-Code approach saved us days of effort
By Lovely Kumari , Raj on 2022-01-04

Image Credit: https://1point21gws.com Introduction We all know why testing is an important part of software development life cycle, especially in agile environment, where release cycle time is shorter - you do continuous build-test-release every week or two. When it come to startups, its even more challenging since startups work on “fail-fast” approach which usually has resource crunch and grows exponentially (at least in the initial phases). You don’t even realize how soon the product gains 10k users from 1.
Privacy Preserving Social Login Using Hypersign
By Vishwas Anand on 2020-11-16
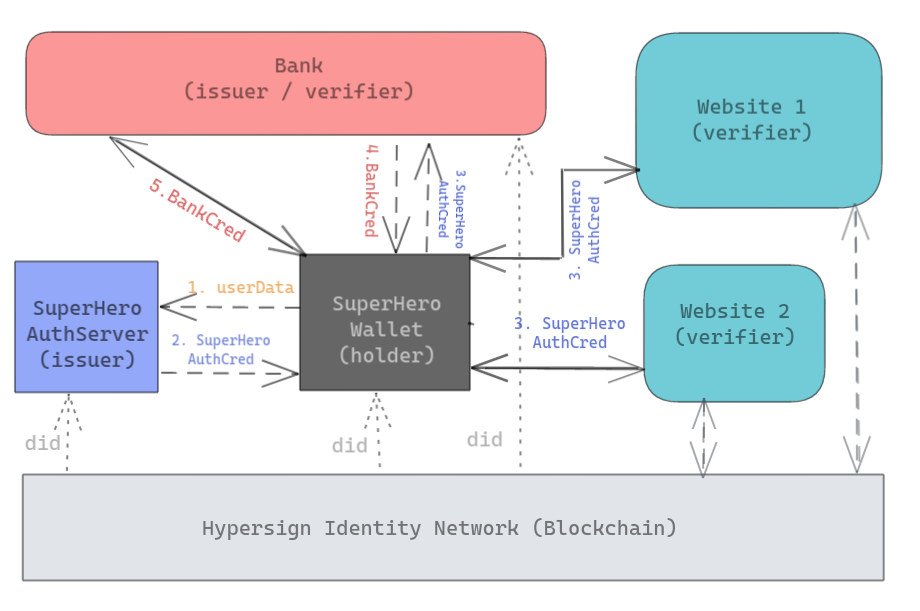
Introduction Social logins like Facebook, Google are common Single Sign-On (SSO) mechanisms for authentication in websites (also called service providers) these days. The social login helps service providers to quickly onboard a user without requiring them to go through the registration process. This way, on one hand, the service providers can provide seamless onboarding to their user and on the other hand, the user need not to type his details like name, email, phone number, every time he avails a service from a new provider.
Data breaches have become common in consumer-facing apps in India; How Hypersign can help?
By Vishwas Anand on 2020-11-02
Abstract The consumer-facing applications are more vulnerable for data breaches as they have a large customer base and they usually stored the user data in a central location. The consumer-facing app provider often has to choose between security and usability and they end up giving priority to the later one as usability become important growth factor. That allows a hacker to steal user data. In this blog, we are going to talk about problems, challenges which service providers face, especially with respect to user data protection and privacy, and what could be possible ways to solve that problem.
