Technical explanation of Two-Way-Authentication; Linking DID with Website Origin
By Vishwas Anand on 2022-06-22
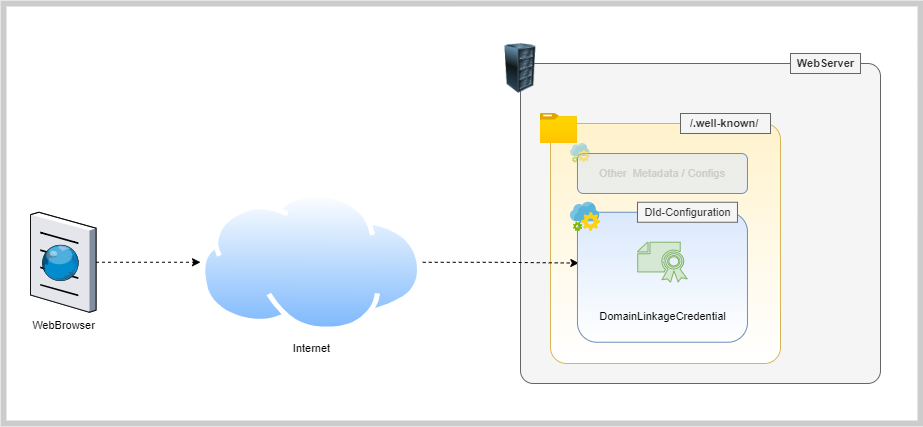
Two features we proudly announce on our website are; Two-Way Authentication and Independent Verification. We will talk about the latter in some other blog but for this blog, let us just stick to the feature - Two-Way Authentication. The question is what is this feature and how it can be technically implemented and proven that it MAY help to stop phishing attacks. Two-Way Authentication Traditionally, when a user tries to log in to a website through a thrid party auth provider (or Identity Provider) like Google Login or Facebook Login, a user is asked to allow access to his/her data by showing him a popup.
Pay per API Call Protocol - Part 1
By Vishwas Anand on 2022-05-18
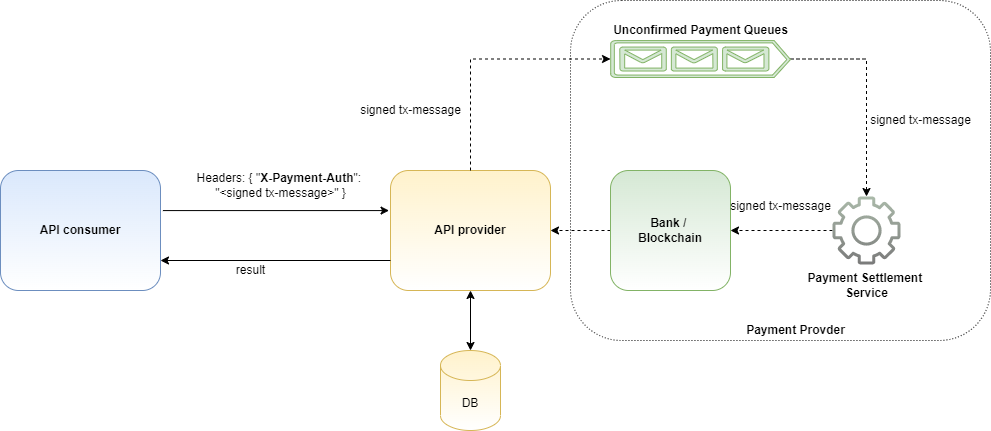
NOTE: This is just my imagination without doing any proper research either on the problem statement or on the protocol. I request you to read this blog keeping that in mind. This is NOT full proof solutinon. Applications share data with each others via APIs. Sometimes, these APIs need to protected behind paywall by the API providers. This is to ensure APIs consumers do not misuse APIs as well as to incure cost of the API services.
Avatars May Use SSI In Metaverse To Prove Identity
By Vishwas Anand on 2022-01-07

Image Credit: https://www.verizon.com Introduction Metaverse has been in the news for quite some time now. Seems like the next “buzzword” after “blockchain” in the tech space. The tech got a surge especially after Facebook decided to change its name to Meta. In this blog, we will understand what is Metaverse (a very basic intro) and its relationship with digital identities. The focus will be on explaining why decentralized digital identities are an important tool for Metaverse to replicate the real world.
Privacy Preserving Social Login Using Hypersign
By Vishwas Anand on 2020-11-16
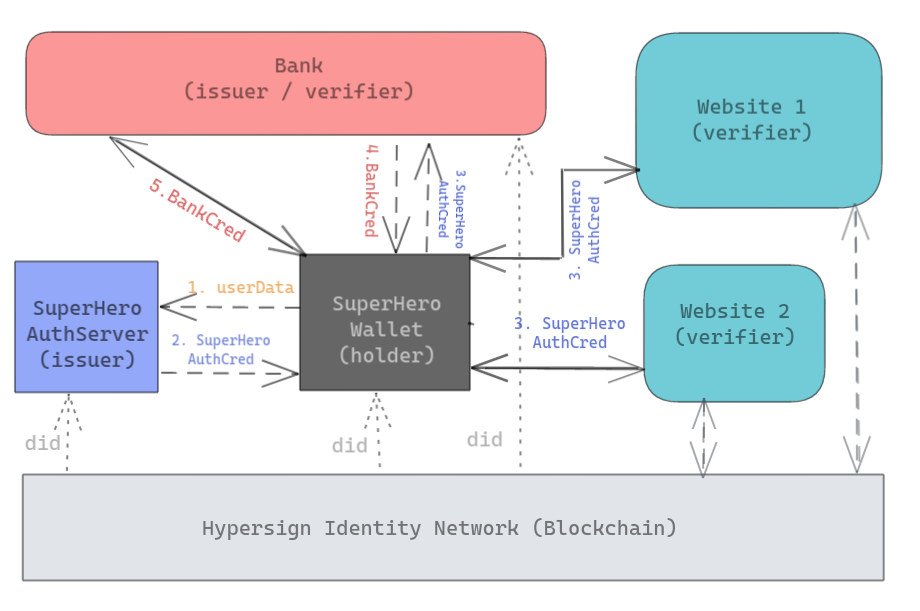
Introduction Social logins like Facebook, Google are common Single Sign-On (SSO) mechanisms for authentication in websites (also called service providers) these days. The social login helps service providers to quickly onboard a user without requiring them to go through the registration process. This way, on one hand, the service providers can provide seamless onboarding to their user and on the other hand, the user need not to type his details like name, email, phone number, every time he avails a service from a new provider.
Data breaches have become common in consumer-facing apps in India; How Hypersign can help?
By Vishwas Anand on 2020-11-02
Abstract The consumer-facing applications are more vulnerable for data breaches as they have a large customer base and they usually stored the user data in a central location. The consumer-facing app provider often has to choose between security and usability and they end up giving priority to the later one as usability become important growth factor. That allows a hacker to steal user data. In this blog, we are going to talk about problems, challenges which service providers face, especially with respect to user data protection and privacy, and what could be possible ways to solve that problem.
Summary of ‘Digital Identity – Foundation for a New Economy’ webinar organised by Citi bank @ 10/22/2020
By Vishwas Anand on 2020-10-23

Introduction Yesterday, I got an opportunity to attend a webinar titles, Digital Identity – Foundation for a New Economy. I was super excited about this webinar since my area of interest is decentralised identity. I found the webinar very insightful and thought that it would be good if I can summarize the session in a blog post so that others (who could not attend) can get benefit of it. Panellist Host Panellist 1 Panellist 2 Panellist 3 Panellist 4 Gary Schneider Arvind Gupta Keit Pentus-Rosimannus David Birch Johan Schmalholz Managing Director at Citi Data & Digital Economy, Platform Policy, New Media & Startups.
Hypersign v1.0 is released; A visual representation of SSI!
By Vishwas Anand on 2020-10-02
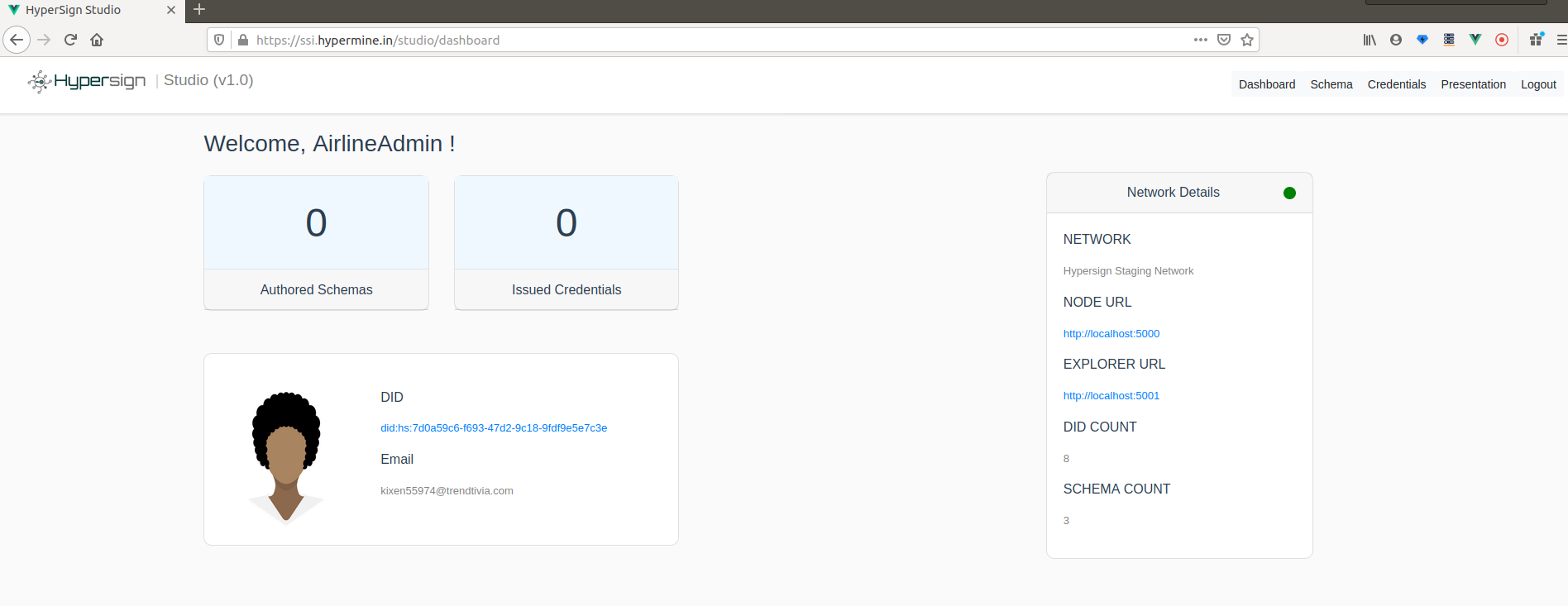
We have been exploring the Self Sovereign Identity (SSI) space for quite some time and today we came up with the first implementation of SSI specification proposed by W3C credential community. Disclaimer This is going to be a long blog since a lot of concept needs to be explain. But I will try to do full justice to your time by explaining SSI with a visual demonstration using a simple use case on Hypersign Studio.
#SSI #digital identity #DID #verifiable-credential #verifiable-presenatation #hypersign
Why blockchain is important tool for SSI (The self sovereign identity) system?
By Vishwas Anand on 2020-09-27
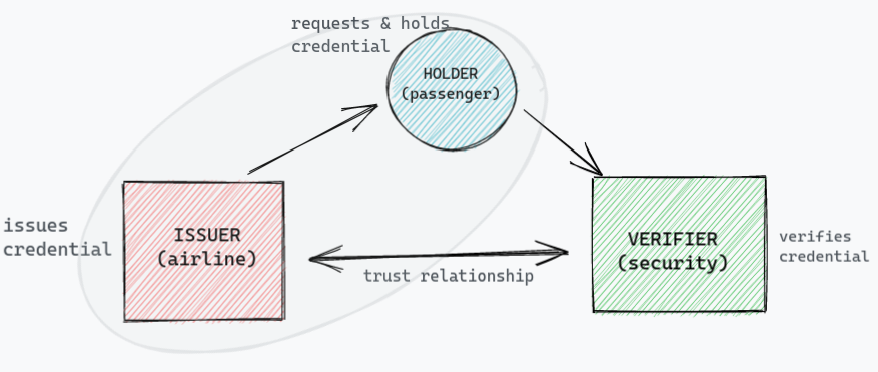
This blog can be considered as a follow-up blog (but not necessarily) of a series of blogs on digital identity. Digital Identity; Past, Present and Future: Where we talked about how digital identity evolved over a period of time and where it is heading to - the SSI. In depth introduction to Self Sovereign Identity (SSI): We took a deep dive into some of the core components of SSI to understand its terminologies and overall architecture.
#SSI #digital identity #DID #authentication #centralised #federated #blockchain #user-centric
Demonstrating Linked Data Signature using Javascript
By Vishwas Anand on 2020-08-03
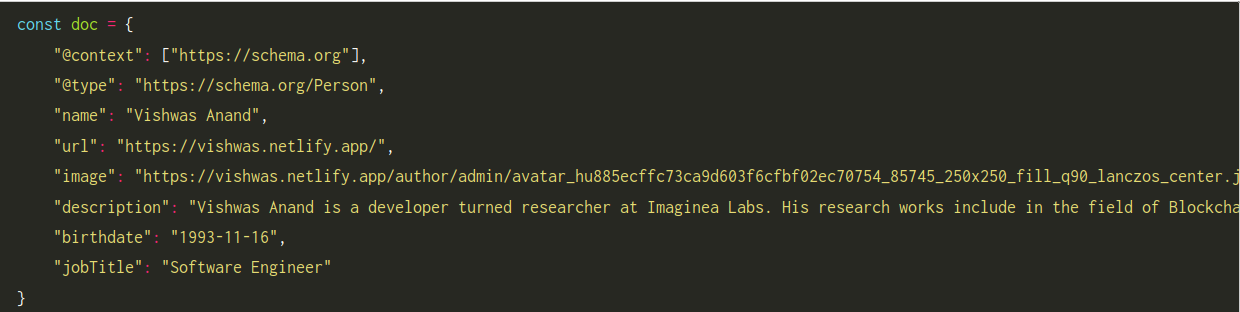
Before we understand what is linked data signature, let us understand what is linked data. Linked Data The term Linked Data is used to describe a recommended best practice for exposing, sharing, and connecting information on the Web using standards, such as URLs, to identify things and their properties. When information is presented as Linked Data, other related information can be easily discovered and new information can be easily linked to it.
In depth introduction to Self Sovereign Identity (SSI)
By Vishwas Anand , Likitha Soorea on 2020-06-14
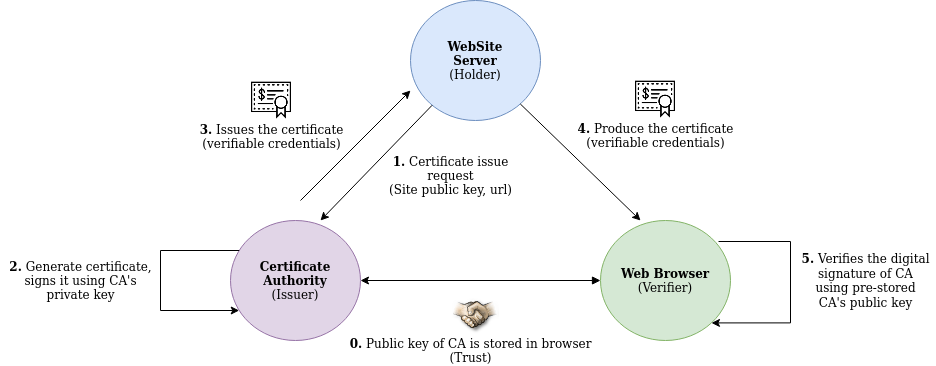
In our previous blog titles - Digital Identity: Past, Present and Future, we went through the journey of digital identity and tried understanding how it evolved over the period and where it is heading. We ended our discussion with the basic introduction of Self Sovereign Identity (SSI) system. If you have not read that blog, I encourage you to read that first before proceeding with this blog. In this blog, we will take a deeper dive into SSI and will try understanding how it works under the hood.
#SSI #digital identity #DID #authentication #centralised #federated #user-centric